Cybersecurity
With proven expertise and a cutting-edge cybersecurity portfolio, NTT DATA serves as your trusted advisor, guiding your business toward secure transformation.
- Overview
- Case studies
- Awards and recognition
- Our impact
- Services in your country
Cybersecurity at NTT DATA – Your Partner for Secure Digital Transformation
Lead innovation through cybersecurity
NTT DATA helps create a safer digital society, enabling our clients to focus on innovation and growth. We provide clients with comprehensive protection against sophisticated threats through our worldwide resources, deep industry insights and advanced technical skills. We enable your business transformation through a coherant global approach, helping you stay ahead of evolving cyber threats and continue growth with peace of mind.
EXPLORE MORE ON WHITE PAPER
NTT DATA’s Global Cybersecurity Services
This article introduces the value that NTT DATA's Global Cybersecurity Services provide as a solution to cybersecurity threats that are advancing and becoming more sophisticated every day.
- Introduction
- Recent Cybersecurity Challenges
- Cybersecurity Capabilities of NTT DATA
- Value Provided by NTT DATA’s Global Cybersecurity Services
- Conclusions

Case Studies
Read how companies in various industries solved their challenges by partnering with NTT DATA.
Workforce Identity & Access Management Solution for Banking Services
Implementation of Identity Governance, Web Access, PAM, and Strong Authentication through the adoption of commercial security solutions for a leading Italian banking group with approximately 25,000 employees.
- - Audit compliance and comply with the European Banking Authority (EBA) guidelines and internal regulations.
- - Automation of assigning user entitlements.
- - Migration from the current custom solution to the identified solution.
- - SSO and access control to simplify user access.
- - Apply strong authentication on all external perimeters during the pandemic.
- - Introduce a PAM solution for all the administrators and critical platforms.
- - Enabling Identity Governance on all target systems in the infrastructure with connected (80) and disconnected (300) target systems. Enable RBAC process (4000 automatic rules) with Oracle Identity Governance
- - Implementation of a Workforce Access Management for employees based on ForgeRock Access Manager
- - Implementing strong authentication with Entrust IdentityGuard for all external perimeters and access to PCs and mobiles
- - Implement a PAM solution for all administrators, RPA users, and system accounts based on CyberArk to manage privileged access to the entire infrastructure
- - Enable full governance of users, entitlements, and roles
- - Using Web SSO (with only 1 account) for all users from Internet and Intranet to access all applications including branch applications
- - Review of all business processes related to identity and access management
- - Fulfilment of compliance and auditing requirements with functionalities included in selected products
- - Increased security and subsequent reduction of operational costs through the adoption of leading IAM solutions
UNECE R156 Consulting, Process Design and Implementation
Customer is a European commercial vehicle manufacturer for heavy duty and medium commercial vehicle classes, as well as for buses. In addition, the company produces and sells engines, both for vehicles, but also for generators or maritime propulsion systems.
- - Assess current processes, roles, methods, tools used by the customer
- - Alignment against regulatory requirements
- - Identification of gaps and proposal of countermeasures to close these
- - Design and define processes, roles and tools needed for regulatory compliance
- - Implementation of processes
- - Support customer in technical audit
- - Fast and detailed overview of gaps in organizational process landscape
- - Roadmap to bring process landscape to audit maturity
- - State-of-the-art know-how of how to define and design compliance processes, roles and methods
Design and implementation of Vehicle Security Operation Center, V-SOC
Our customer is one of the largest suppliers of premium and luxury cars and one of the world's largest commercial vehicle manufacturers. They offer financing, leasing, fleet management, investments, insurance brokerage and innovative mobility services.
- - The establishment of a V-SOC to monitor vehicle fleets against potential hacker attacks.
- - In order to properly receive data from the vehicle and take into account the data protection requirements of customers (ex. anonymization), a micro-service must be developed to "translate" data.
- - In order to also be able to reverse anonymized data in the event of a real attack.
- - Design and implementation of a V-SOC for the client:
- - Implementation of on-board IDS systems.
- - Creation of processes, runbooks, etc. to respond to incidents in the SOC.
- - Definition of threat intelligence for early threat detection.
- - Development of a hash function for the anonymization and de-anonymization of data.
- - Development of functions for translating in-car data into a readable human and SIEM-readable format
- - Attacks on vehicles are detected at an early stage and can be stopped.
- - Protection against fleet attacks with high financial damage and reputational damage.
- - Prehensive detection of vulnerabilities leads to more efficient remediation.
- - Data protection requirements are taken into account.
- - Cryptic CAN data is easy for humans to read.
- - Lean Micro-Service solution is cost and maintenance efficient.
For an International automobile manufacturer, design and delivery of a solution for Plant Security
One of the largest Japan’s automobile manufacturer with about 1,000 subsidiary companies and affiliates involved in the production of automobiles, automobile parts, and commercial and industrial vehicles.
- - Focus on the design, implementation and operation of cyber security controls for the European plants.
- - Security Maturity Assessment of 8 plants across Europe.
- - Analysis of cybersecurity impacts on human lives, operations and product quality.
- - Define policies and management procedures for Asset Management.
- - Define roles and responsibilities for operations activities.
- - Design the architecture to allow secure remote access support.
- - Define monitoring perimeter and OT Detection solution.
- - Implementation of Incident Management practices.
- - NTT DATA has gathered an international team with specialists from various European countries to meet the customer's needs which Italy plays a key role.
- - Highly challenging project demanded multidisciplinary skills involving the fields of industrial automation, safety and security.
- - NTT DATA accredited as a company capable of covering the gap between business needs and production aspects.
- - Demonstrated in-depth knowledge of industry security standards, specifically ISA/IEC 62443 and NIST 800-82r2.
- - Enable transformative Industry 4.0 innovation technologies to increase productivity and operational efficiency in a secure manner.
- - Enable a secure integration between OT and IT systems (Manufacturing Execution System and Enterprise Resource planning).
- - Better understanding of the causes that can lead to a disruption and its possible impacts.
- - Accurate, centralized and automatically updated inventory of company assets.
- - Proactive cyber risk detection and effective incident response.
- - Secure remote working with managed and monitored infrastructure access.
Cloud Security Migration
North American FORTUNE 200 company that is one of the world’s largest consumer products companies. It operates worldwide and is supported by an employee base of approximately 7,000 employees.
- - Securely architected Azure Cloud instance
- - Migration to the Cloud
- - Accommodation of Client’s architecture and core technologies to enable Client’s Cloud strategies, agile adoption, and?automation focus, while complying with Client’s security, risk management, and governance policies.
- - Cloud Security Managed Services
- - NTT DATA provided Architecture design of secure Azure Cloud
- - Securely configured and implemented new Azure Cloud instance for Client.
- - Providing Cloud Managed Services including Security Managed Services
- - Cloud Security Managed Services include Azure AD, Key Vault, Secure Configurations, Microsoft Defender for End Point, Microsoft Defender for Cloud, Container Security/Encryption, Managed Firewalls, VPN, Compliance and Remediation, Network Access Control
- - In the process of deploying Microsoft Defender for Identity
- - Implemented best practices to optimize SOP
- - Providing Security Architecture Services
- - Automate remediation/self-healing
- - Service Level Improvements
- - Shift left/improve resolution timeframes
- - Decrease support costs and helpdesk tickets
- - Next Generation solutions/improved security posture
- - Support model optimization
- - Scalable growth
- - Protection of hybrid environment
- - Thought leadership and innovation through continuous improvement process
- - Reduction/Prevention of Shadow IT
Managed Security Services
Global healthcare solutions company that incorporates product manufacturing, distribution support, and innovative technology services. FORTUNE 500 company with operations located across North America, Asia, Europe, and Latin America with 15,000 employees.
- - Consolidate multiple Business Unit’s into one secure infrastructure
- - Business Partner who is not just an “Order Taker”
- - Complex enterprise operating?environments, different process, capability & taxonomy
- - Different security solutions within Business Units
- - Reduction in circuit costs, software and hardware licenses and support
- - Reviewed list of solutions and recommended tool consolidation or transformation to next generation solutions such as SASE
- - Provided Information Security Manager to provide Service Delivery Management, contract governance and thought leadership
- - Migrated current infrastructure to Hybrid Cloud
- - Reviewed current processes and improved and expanded capabilities at a lower cost
- - Solutions include IAM, SOC/SIEM, Threat Hunting, Incident Response, Vulnerability Management, Key Management, Azure AD, SSO, MFA, Cert Management, EDR, PAM, WAF, Next Gen Firewalls, VPN, SASE and UAA
- - Significant savings in reduction of circuit costs with implementation of SDWAN/SASE
- - Cost reduction by tool consolidation
- - Next Generation solutions/improved security posture
- - Improved Support Model
- - Thought Leadership and Innovation
- - Service Level Improvements
- - Operational Improvement
- - Improved Incident Handling and Response
Customer Identity and Access Management Solution for Banking Services
Leading Italian banking group with approximately 25,000 employees and 5,000,000 retail customers. Implementation of SCA, 3DS, SCA functionalities through the adoption of commercial security solutions
- - Enable customers access control infrastructure in compliance with the PSD2 directive and other compliance requirements
- - Support and protect credit cards payment mechanisms (3DS and 3DS2)
- - Introduce Strong Customer Authentication (SCA) and Dynamic Linking mechanisms for transactions
- - Support more than one SCA methodology including Fallback solutions
- - Increase security levels by replacing custom components with market solutions
- - Make the solution easily scalable in order to handle a growing workload.
- - Migration from the current custom solution to the identified solution
- - Implementation of the new access control infrastructure and Strong Customer Authentication solution. Modification of the new onboarding processes of the new infrastructure.
- - Use of ForgeRock Access Manager to handle access control and of Entrust IdentityGuard for SCA
- - Introduction of the Dynamic Linking feature on all devices
- - Risk-based authentication: Integration with the anti-fraud engine both during the authentication (login) and authorization phases (including handling of additional authentication factors if needed)
- - Introduction of standard protocols such as OpenID and SAML
- - Decrease of login time with a 5:1 ratio between custom and commercial product.
- - Increase of security and decrease of operating costs through the adoption of market solutions.
- - Simplification of patch management processes
- - Decrease of go-to-market times for access control and authentication features
- - Fulfillment of compliance and auditing functionalities already considered for commercial products
Network Visibility and Threat Detection in OT
Leading chemical and pharma company based in Germany. It operates about 60 production sites globally for pharma and crop science and has more than 99,000 employees
- - Significant increase of cyber attacks
- - Regularity requirements as part of European critical infrastructure
- - Business requirement to improve the visibility and transparency of the complex Operational Technology (OT) environment
- - Regulatory requirement to improve security of pharma production sites.
- - Strategic goal of extending Industry 4.0 architectures and resulting increase in cybersecurity risks
- - Different OT technologies in different countries
- - Lack of security know-how in factories.
- - No global OT security alignment
- - Global rollout of OT threat detection solution including: Architecture, Site preparation, Shipping support incl. tax handling, Local installation and configuration, Alert tuning, Local training of sites, SOC connectivity
- - Global collaboration of NTT DATA’s OT security teams
- - Local support in more than 20 countries
- - Asset discovery, risk assessment, vulnerability assessment for the production site
- - Analysis of traffic flow
- - Connectivity to customers SOC and implementation of OT SOC processes
- - NTT DATA finished global rollout of OT threat detection and visibility solution
- - Complete Assets inventory (Visibility) in OT of all production sites
- - OT Threat Detection incl. SOC alerting up and running
- - Operational SOC services for all OT sites.
- - OT Security improvements
- - Technical risk assessment
- - Risk mitigation strategy
- - Fulfilment of regulatory requirements

Bayer Brings Its Manufacturing Operations' OT Security Up To Date
In collaboration with Bayer AG, we enhance cybersecurity for their global Pharmaceuticals Division's complex operational technology (OT) environment. Using Guardian appliances and Central Management Console from Nozomi Networks, our experts boosted asset visibility and protected critical infrastructure. We expanded asset availability across 15 major sites in globally.

Workforce Identity & Access Management Solution for Banking Services
Implementation of Identity Governance, Web Access, PAM, and Strong Authentication through the adoption of commercial security solutions for a leading Italian banking group with approximately 25,000 employees.

UNECE R156 Consulting, Process Design and Implementation
NTT DATA helped a European commercial vehicle manufacturer define and design compliance processes, roles and methods to get certified in UNECE Regulation (R156).

Design and Implementation of Vehicle Security Operation Center (V-SOC)
One of the largest suppliers and manufactures of luxury cars needed to establish a V-SOC to monitor against potential hacker attacks. NTT DATA helped design and implement it with on-board IDS systems, processes, runbooks, and more.

Design and Delivery of a Solution for Automobile Plant Security
NTT DATA assessed the security maturity of eight plants across Europe for one of the largest Japanese auto manufacturers and helped them design and implement the cyber security controls for the plants with industry security standards, such as ISA/IEC 62443 and NIST 800-82r2.

Cloud Security Migration for North American FORTUNE 200 Company
NTT DATA provided a consumer products company with architecture design of secure Azure Cloud, including AzureAD, Key Vault, Secure Configurations, and many more.

Managed Security Services for a Global Health Solutions Company
NTT DATA helped a FORTUNE 500 health solutions company implement managed security services with NTT DATA’s own Hybrid Cloud, IAM, SOC/SIEM, Threat Hunting, and more, and improve security posture with the next generation solutions.

Customer Identity and Access Management Solution for Banking Services
A leading Italian banking group needed to enable customers’ access control infrastructure in compliance with PSD2 directive, and NTT DATA helped them implement it with a Strong Customer Authentication solution, including ForgeRock Access Manager and Entrust IdentityGuard.

Network Visibility and Threat Detection in Operational Technology
NTT DATA provided a leading chemical and pharmaceutical company in Germany with operational technology threat detection solution, including architecture, site preparation, installation, training, and more with local support in more than 20 countries.
Our Services
NTT DATA provides integrated security services from strategy to operations and incident response on a global scale.
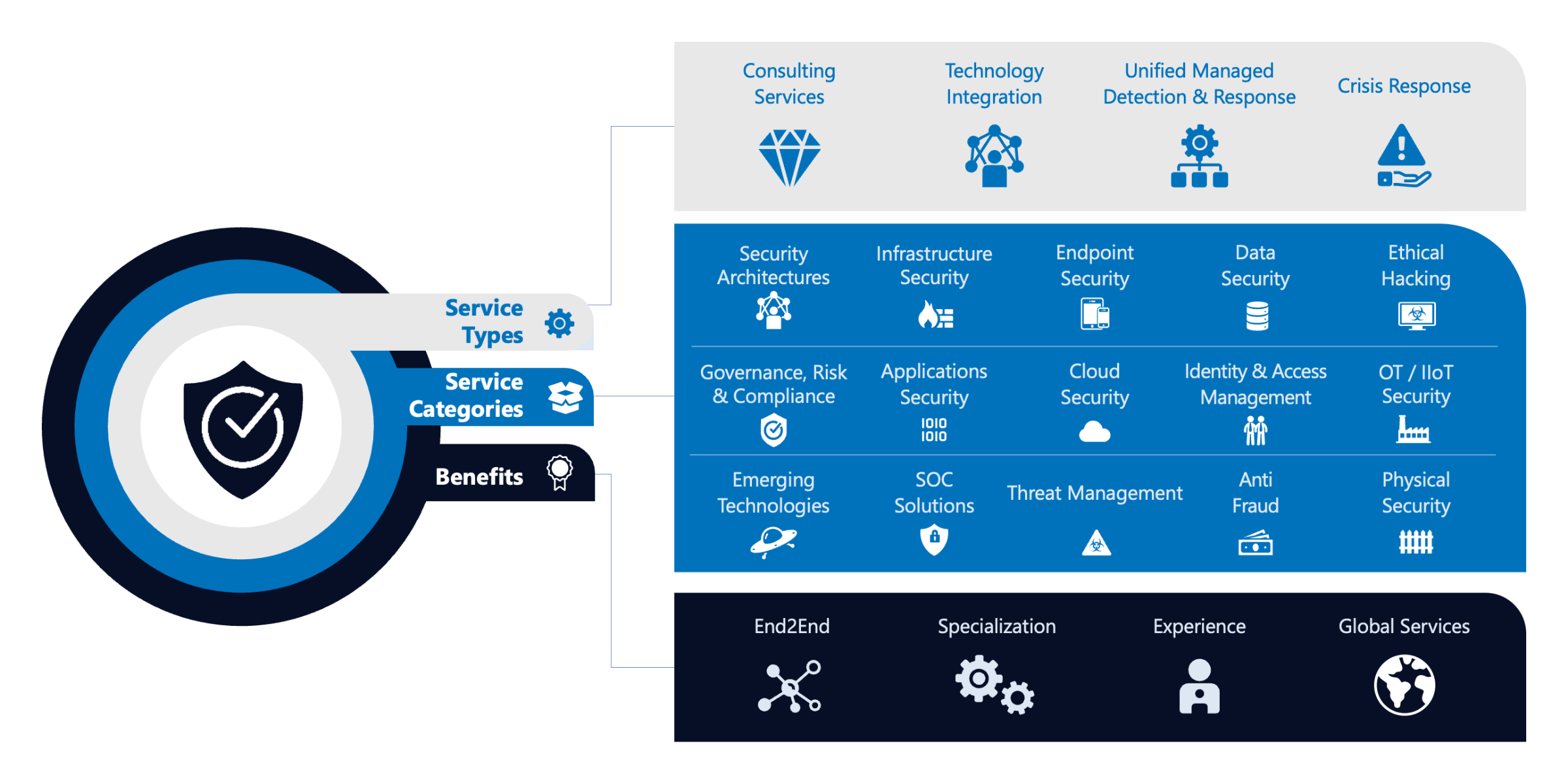
Consulting Services
Help businesses and organizations identify opportunities, solve complex problems, and design effective solutions.
Technology Integration
Set up and customize software platforms to meet the specific needs and requirements of a business or organization.
Unified Managed Detection & Response
Continuously identify, assess, classify, remediate and mitigate security weaknesses, including root-cause analysis.
Crisis Response
Fast crisis response and recovery services in case of a sudden cybersecurity incident.
Zero Trust Implementation by NTT DATA
NTT DATA has years of experience with Zero Trust security. We can help you implement a Zero Trust security model based on proven technologies that are suitable for your company by combining multiple services of our portfolio.
Zero Trust is a security model based on a principle, “never trust, always verify.” It enables companies to get rid of tedious and expensive security controls and build a more dynamic and efficient technological platform that is tailored to their customers and their business needs.

Our Partners
NTT DATA has strategic partnerships with vendors and can provide the appropriate solution to meet your requirements.











V-SOC – Effectively and efficiently, protect networked vehicles against cyber attacks (2:40)
Resource Library
Explore our latest research, insights, and news on the crucial topics in cybersecurity.

BLOG: NTT DATA FOCUS
Participation and sponsorship of the 36th Annual FIRST Conference

BLOG: NTT DATA FOCUS
Potential use of Generative AI in risk analysis operations

BLOG: NTT DATA FOCUS
Generative AI used in incident response

BLOG: NTT DATA FOCUS
Strengthen Security with SBOM in the Automotive Industry!

Automotive Security Testing

BLOG: NTT DATA FOCUS
Security Risks of Generative AI and Countermeasures, and Its Impact on Cybersecurity
- BLOG: NTT DATA FOCUS The role of automation in cybersecurity operations
- NEWS NTT DATA Enters Into Global Strategic Application Security Agreement with Synopsys Software Integrity Group
- BLOG: NTT DATA FOCUS Tips for Co-creating Security Services with Startups
- BLOG: NTT DATA FOCUS Improve Supply Chain Security through Visualization of Software Components Using SBOM
- BLOG: NTT DATA FOCUS NTT DATA Global Efforts to Increase Cybersecurity Professionals
- NEWS NTT DATA and CYFIRMA Announce Global Strategic Partnership in the AI-powered Cyber Threat Intelligence Field
- WHITE PAPER Towards Migration to Secure Information Infrastructures Even in Quantum Computers Era (PDF: 1,6MB)
- WHITE PAPER Automotive Cybersecurity (PDF: 2.6MB)
- NEWS NTT DATA Introduces New Global Cybersecurity Strategy to Help Clients Boost Protection Against Cyber Risks
- NEWS NTT DATA Launches Security Management Outsourcing Service
- BLOG: NTT DATA FOCUS You can only protect what you know - The importance of OT environment visualization
- BLOG How to Adopt Modern IDS and VSOC for Your Vehicle's Security
- INSIGHT VIDEO Protecting Networked Vehicles Against Cyber Attacks with NTT DATA’s V-SOC
- BLOG VSOC Is the New Safety Gear for You and Your Vehicles
- ARTICLE The Human Side of Risk
- BLOG Strengthening Security Programs Through a Human-Centric Focus
- NEWS NTT Group participates in Locked Shields 2023, an international cyber defense exercise organized by NATO CCDCOE
Awards and Recognition
NTT DATA has been recognized for its innovative use of technologies and solutions that help customers drive innovation. Explore the details of each recognition and award below.

Major Player in IDC MarketScape: Worldwide Systems Integrators/Consultancies for Cybersecurity Consulting Services 2024 Vendor Assessment
Read the assessment
- Gartner ® Recognition / 2024 * Ranked #1 by Revenue in the 2024 Gartner Competitive Landscape: CSP Managed Security Services 2024
- Rubrik / 2024 Emerging GSI Partner of the Year award 2024
- Everest / 2023 Major Contender in Everest Cloud Security services PEAK Matrix® assessment 2023
- Claroty / 2024 Global Partner of the Year
- Everest / 2023 Leader in Everest Risk & Compliance in BFS IT Services PEAK Matrix® Assessment 2023 (PDF: 1.5MB)
- Google Cloud / 2023 Rising Star Award (Security)
- Everest / 2023 Major Contender in Everest Managed Detection and Response (MDR) Services PEAK Matrix® Assessment 2023
- Cisco / 2023 Multiple partner awards
- Everest / 2023 Major Contender in Everest Identity and Access Management (IAM) Services PEAK Matrix® Assessment 2023
- CrowdStrike / 2023 Central European Technical MVP Partner Award
- Gartner ® Recognition / 2022 ** Ranked #2 by Revenue in the 2024 Market Share Analysis: Managed Security Services, Worldwide, 2022
- Exabeam / 2023 Partner of the Year 2023
- Everest / 2022 Major Contender in Everest IT Security Services PEAK Matrix® Assessment 2022 - North America
- Okta / 2023 APJ Customer Identity Cloud Partner of the Year 2023
- Everest / 2022 Major Contender in Everest IT Security Services PEAK Matrix® Assessment 2022 - Europe
- Palo Alto Networks / 2023 2023 SASE Partner of the Year for North America and SI Partner of the Year for EMEAL
- Zscaler / 2023 EMEA Systems Integrator of the Year 2023
- * Gartner, Competitive Landscape: CSP Managed Security Services, 24 April 2024.
- ** Gartner ® , Market Share Analysis: Managed Security Services, Worldwide, 2022, 19 May 2023.
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved. Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner's research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
Our Impact
Cybersecurity Professionals
NTT DATA currently employs more than 7,500 security professionals highly specialized in various industries and technologies around the world.
Cybersecurity Delivery Centers
NTT DATA has more than 80 cybersecurity delivery centers worldwide and can provide solutions to meet cost and regulatory compliance requirements.
Security Operations Center facilities
NTT DATA have security operation centers (SOCs) globally, enabling us to support customers wherever they are in the world.
Years of Cybersecurity Experience
NTT DATA has more than 30 years of cybersecurity service experience.
Global Threat Intelligence
NTT DATA leverages global threat intelligence gained from analytics of over 40% of the global internet traffic in NTT backbone.
Cybersecurity Services in Your Country
We provide our cybersecurity services in the following countries. Follow the link to find out what specific services are available in your country.
NTT DATA Services
NTT DATA EMEAL
NTT Ltd.
NTT DATA

For Other Services
Select a country below to explore other services and solutions available in your country.
Select a country
Quarterly Report on Global Security Trends
NTT DATA’s CSIRT (Computer Security Incident Response Team), NTTDATA-CERT, publishes a quarterly report on global security trends from its own perspective to keep the industry up-to-date with current and future cybersecurity information.
Quarterly Report on Global Security Trends: 2nd Quarter of 2023
- Featured Topic: Revisions related to cloud services in the government security common standards, FY2023 edition
- Featured Topic: Digital ID wallets
- Threat information: Cyberattack incidents targeting Microsoft Teams users
- Threat information: Escalation of cybercrime through generative AI chatbots and deepfakes
































